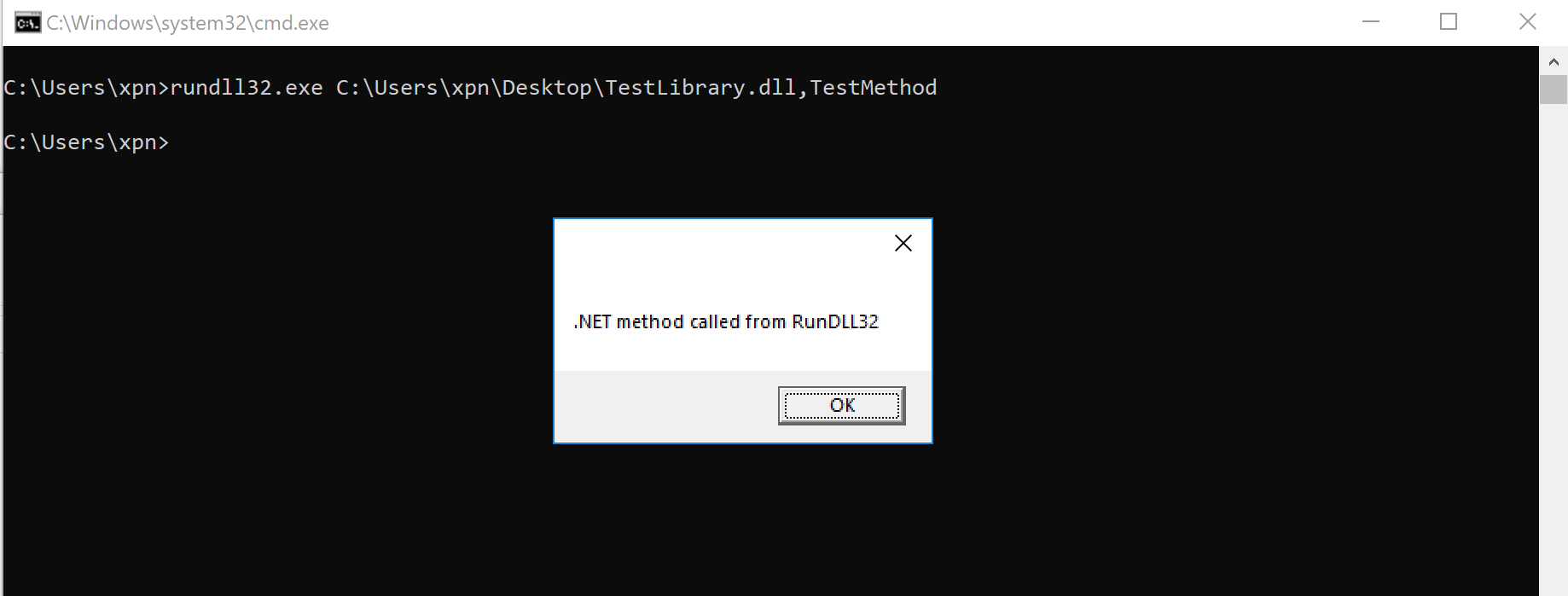
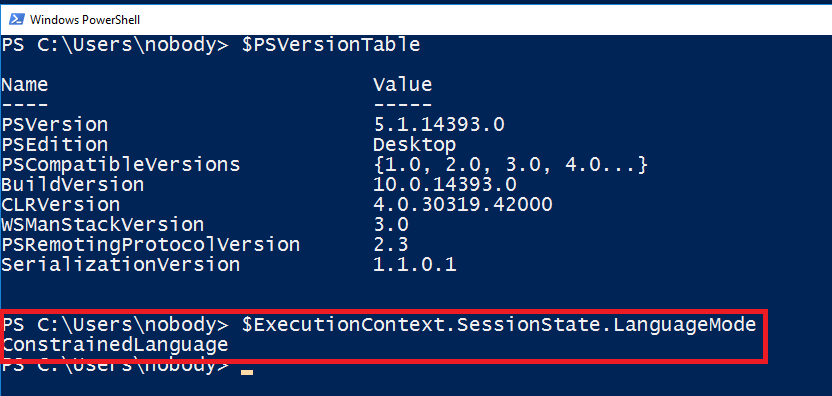
ActiveBreach, powered by Ethereum Blockchain

I’m not actually sure when the abstraction of Blockchain started or when it became such a marketing buzzword, but with so many things claiming to be “Powered by The Blockchain”, I wanted to dig into the technology to understand if there was any benefit to be had by an aggressor.... Read More »