Universal XSS via Evernote WebClipper
During an evening of bug hunting, I found a cool issue in Evernote's WebClipper tool. The result was a Universal XSS vulnerability, which we will explore in this post.... Read More »

During an evening of bug hunting, I found a cool issue in Evernote's WebClipper tool. The result was a Universal XSS vulnerability, which we will explore in this post.... Read More »
In this post, we will continue to explore driver exploitation, focusing on NULL pointer dereferences, and demonstrating how we can exploit this class of vulnerability on both Windows 7 x64 and Windows 10 x32.... Read More »
Following on from my earlier post in which we walked through creating an exploit for the WARBIRD vulnerability, over the next few posts I'm going to be looking at Windows kernel exploitation. If you haven't had chance to read it, I'd recommend that you pause and give it a quick glance as some of this walkthrough will rely on concepts introduced previously. This post will start off by laying the groundwork for future posts, and walking through a simple stack overflow... Read More »
This week I took a break from SYSTEM chasing to review some anti-debugging techniques. With quite a few Bug Bounty programs available relying on client-side applications, I thought I'd share one of the techniques used by numerous security products (and apparently game anti-cheat engines) to stop you from debugging core components, and just how we can go about bypassing this. Obviously it goes without saying, but the technique shown in this post is not a vulnerability, if an attacker has this le... Read More »
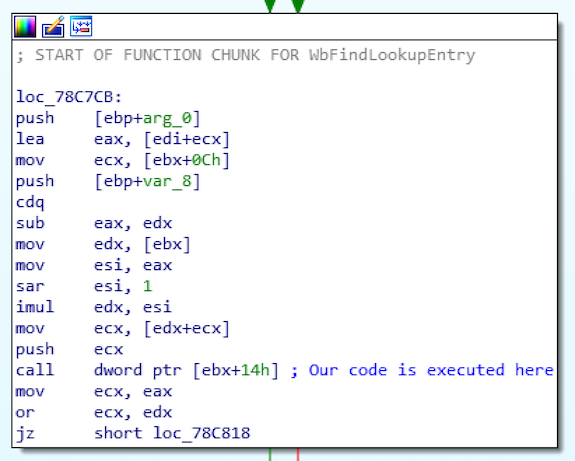
In this post I wanted to take a look at something which I touched on previously, and that is just how a Windows kernel based exploit achieves privilege escalation. Rather than take something like HackSys Extreme Vulnerable Windows Driver, I wanted to work on something a little bit different... Read More »