The .NET Export Portal
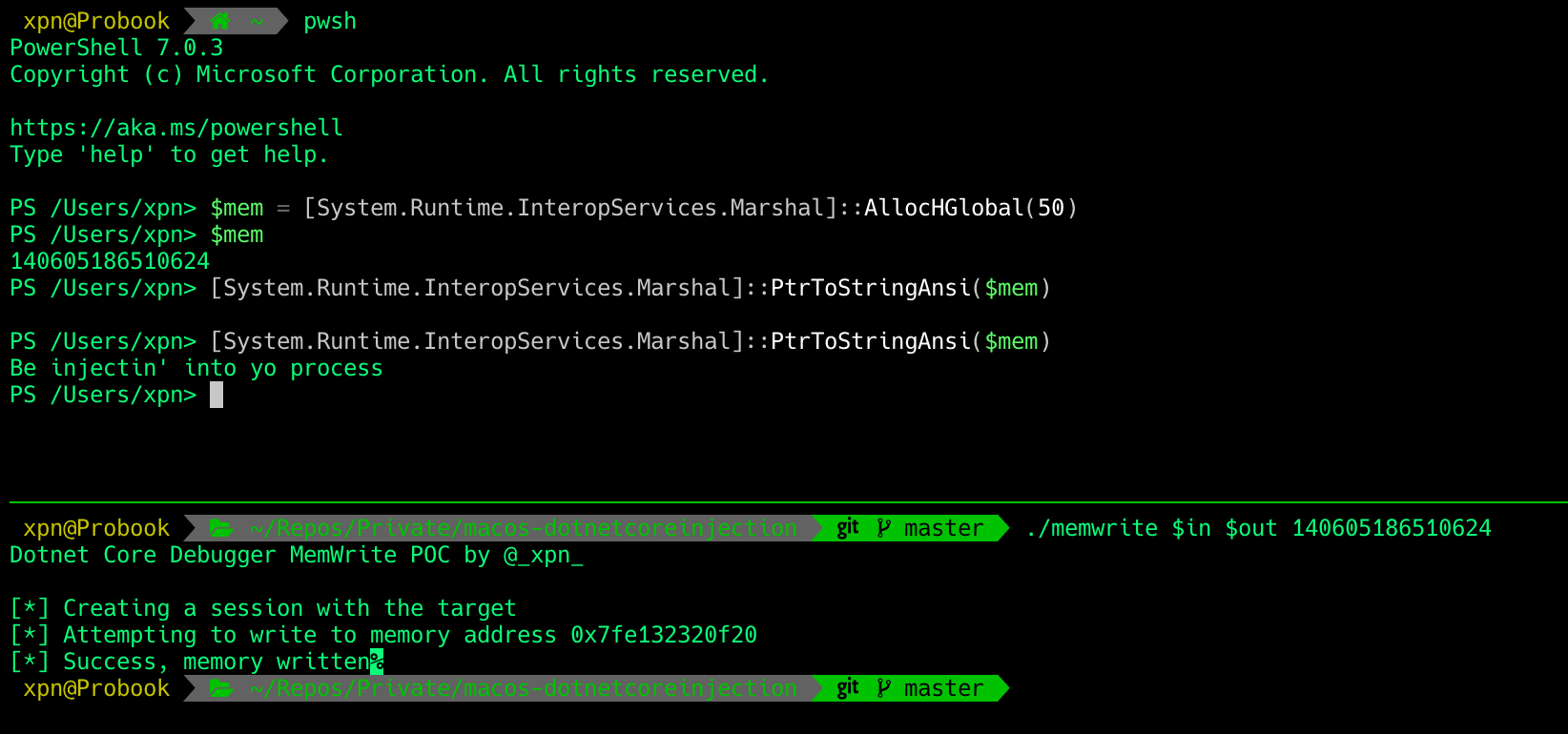
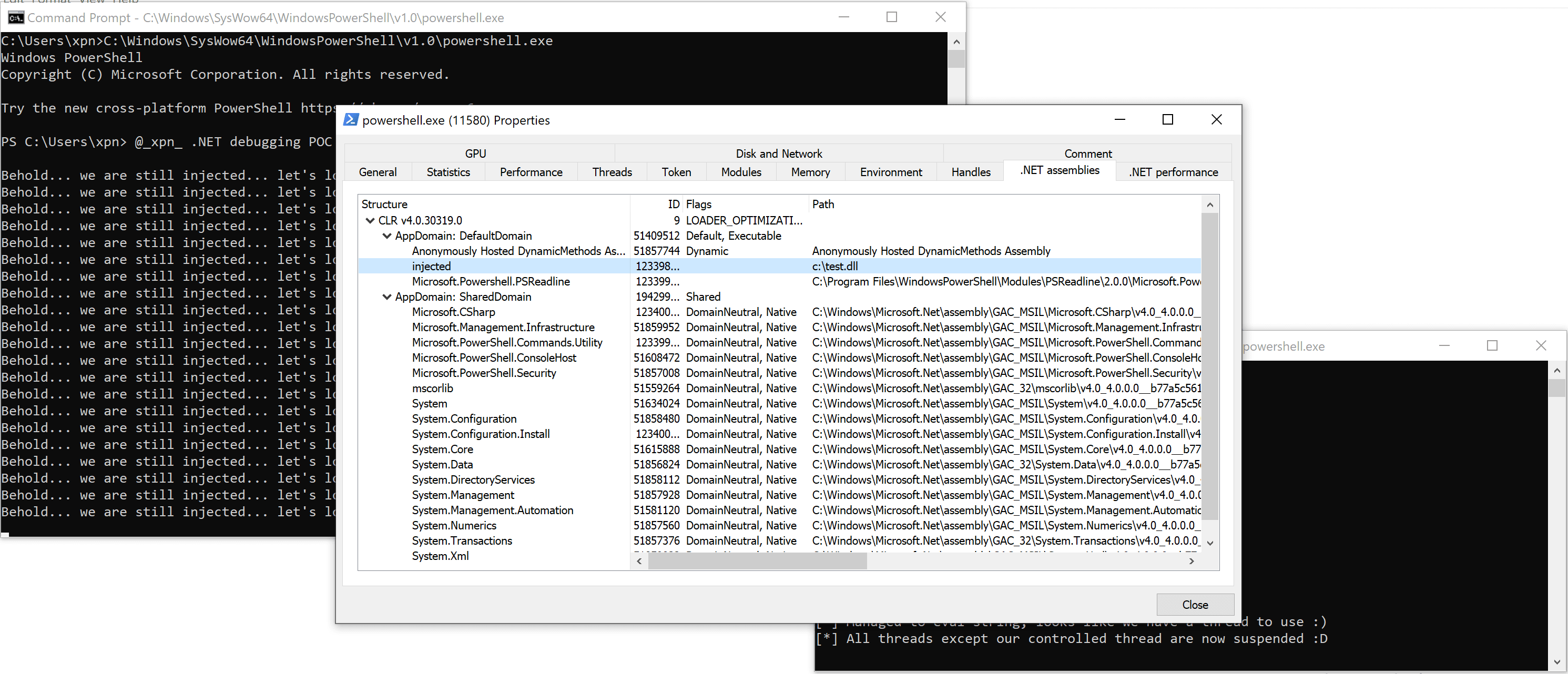
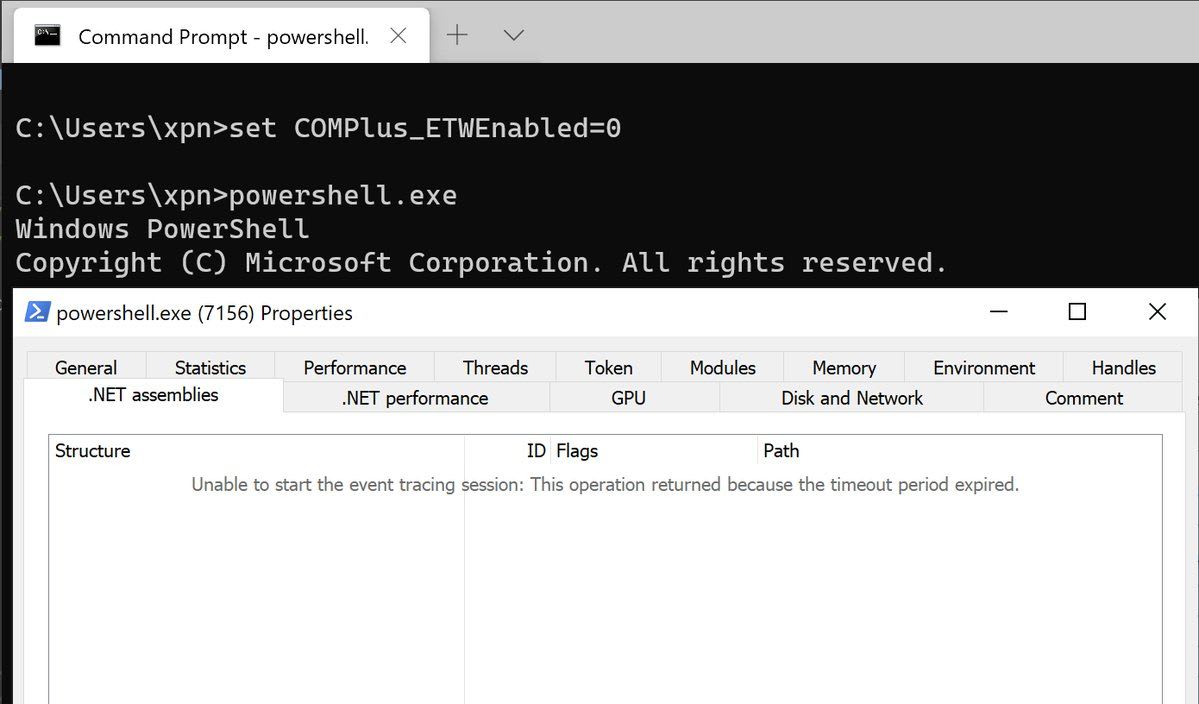
While working on some tooling recently I revisited the topic of .NET unmanaged exports and wanted to know just why this works in the way that it does. After all, by now we've all seen the COM calls required to spin up the CLR, so what makes unmanaged exports so special?... Read More »