Defcon 25 in Review

This year I attended Defcon for the second time. I live in the UK, so making it out to the US for this awesome conference is something that I look forward to throughout the year.
As part of my day job I’m a penetration tester, and I actually found myself in Santa Clara the week before Defcon on an assessment. Due to some unique circumstances, I took what I think must be a record breaking detour back to Defcon. After checking out the local famous garages and technology spots, I was on a flight back to the UK:
Landing in Manchester airport on the Monday, I was packed and ready to fly back over to LV for Tuesday afternoon:


This year I attended the conference with some of the other hackers from Secarma. Seeing what the conference had to offer in terms of CTF challenges the year before, we went with the intention of competing in a few of the competitions, and had decided to take a look at the IOT Village who we knew were running an 0day track.
But before Defcon started I had some free time, and the awesome guys n’ gals at BugCrowd asked me if I would like to drop by their Blackhat booth and meet some of the researchers on the platform, talk with some people who may have questions, and generally just hang out.
Over the days of the conference, I got a taste of what Blackhat had to offer, and met some awesome hackers including TheLaytonCipher, Darkarnium, Bader and of course some of the resident Bugcrowd crewe, the brilliant Sam, Keith, Abby, Zoe, and of course Casey.


Bugcrowd certainly know how to throw a party, seeing us on the top floor in the Skyfall Lounge with some pretty epic views, and allowed us to catch up and share a few beers with our old friend Mr Helme and his entourage :)


But before long, it was time for Defcon, and LineCon 2017 commenced:

Ask anyone what they enjoy about Defcon, and you will get some crazy and profound answers. For me, sitting around with a bunch of hackers, techno music and low neon lighting is pretty much what I’m there for, and the IOT Village had all of this:


We pretty much spent most of our time in this village, except for the evenings when we were continuing to work on the 0day competition in the hotel rooms of LV with a makeshift rig of IOT devices, some networking setup, and beer:

What I love about this atmosphere is that it draws people in to areas that they have never considered before. Our core “CTF” team started as 4 people, Sam, Lor, Dan, and myself.
Shortly after entering the IOT Village, that team expanded to include a number of Secarma members who were there to party - Kyle, Jed, A hacker who values his privacy, and our faithful leader Mark.
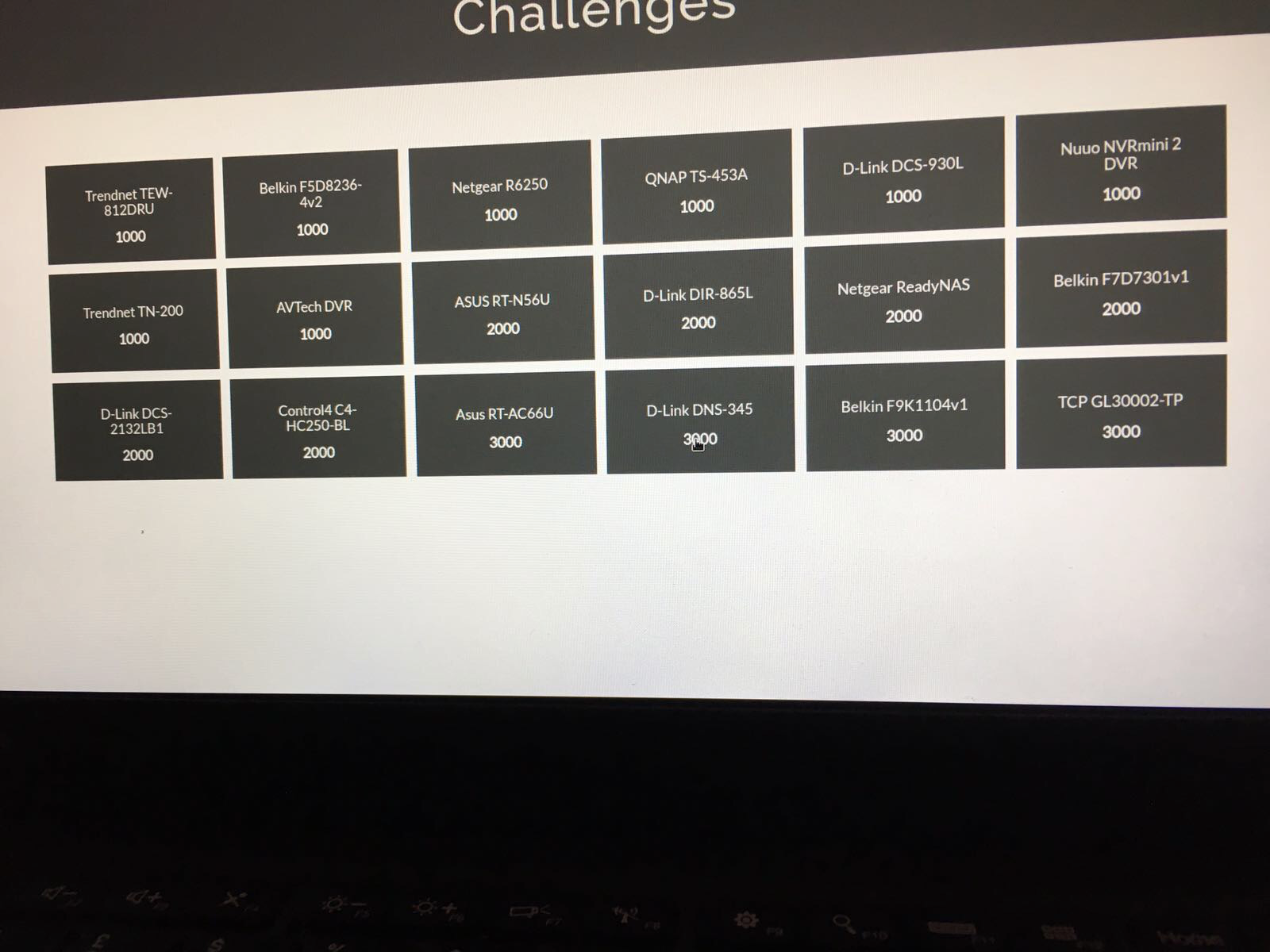
Already knowing that we would be competing to find as many 0days as possible in IOT devices, we also wanted to take part in the running CTF that was being hosted by SOHOpelesslyBroken. This consisted of multiple networked IOT devices, routers, lightbulbs, NAS devices, DVRs etc.. with the challenge being to compromise every device on the network remotely.
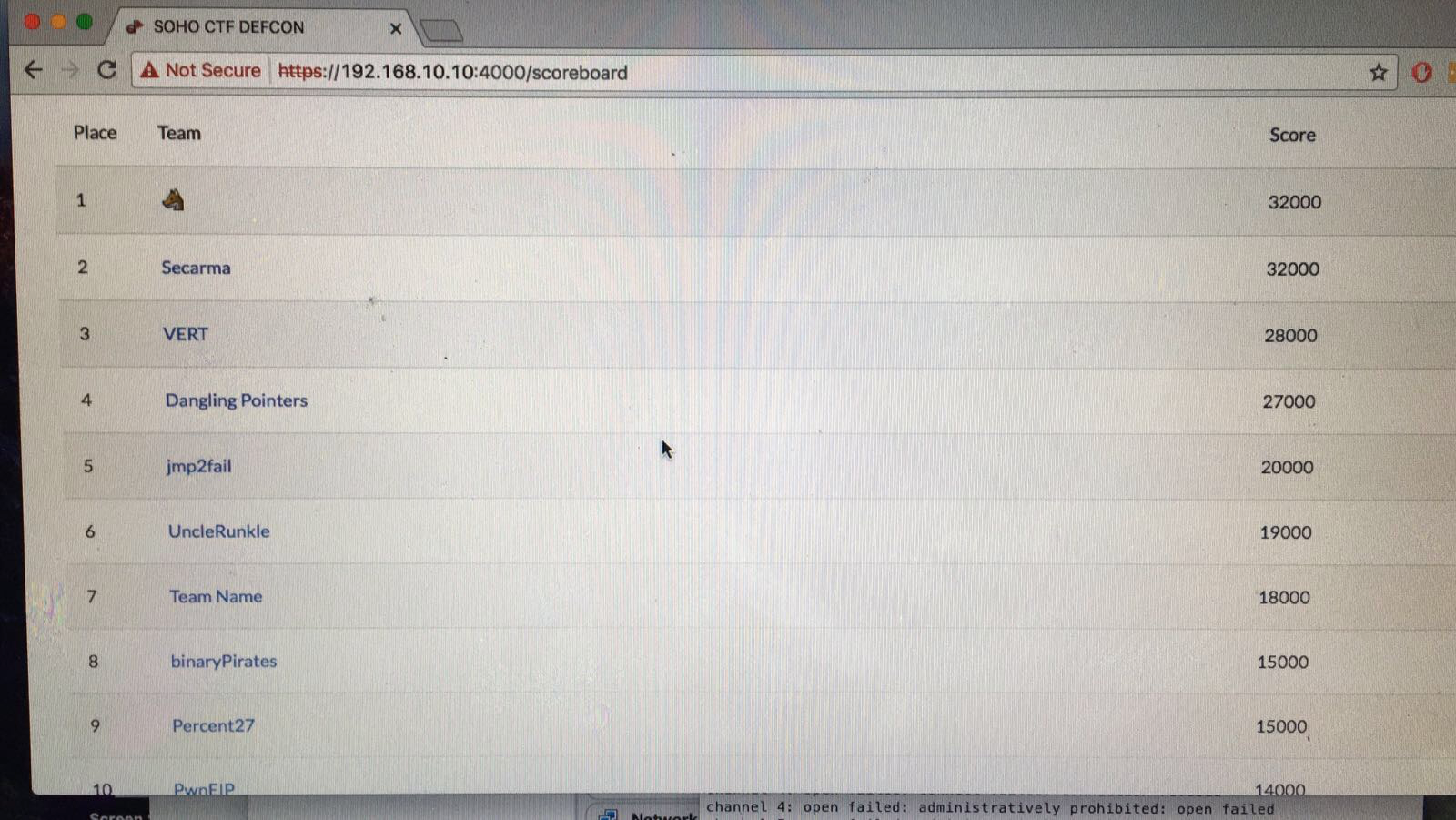
The scoreboard looked like this:
By the time we were done, our scoreboard looked like this:
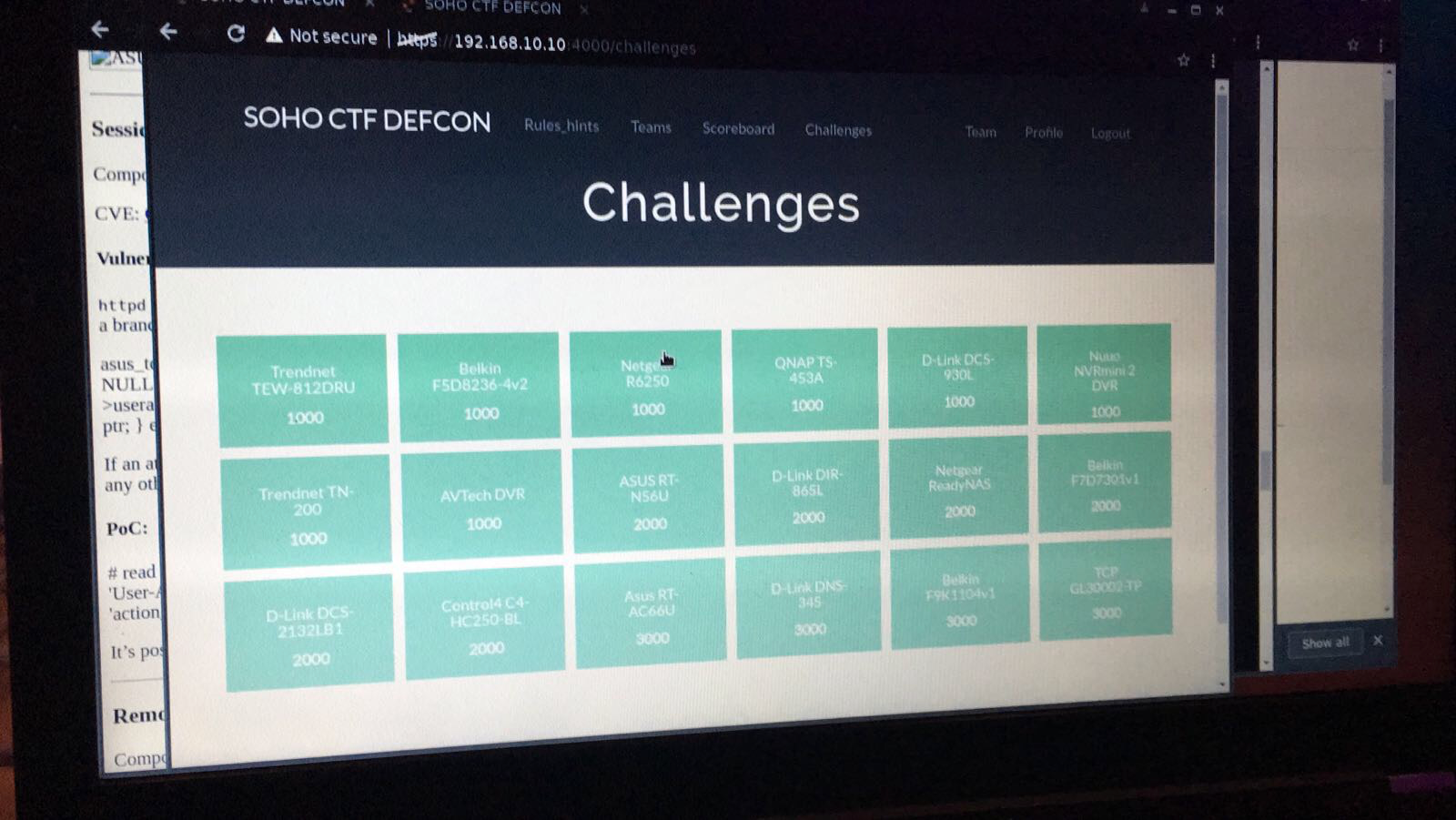
We were pipped to the post by Team Wolf Emoji, finishing up in second place, but we cleared the board and thankfully managed to compromise each device.
With the 0day track, we did quite well, identifying 10 previously unknown vulnerabilities. Receiving the results, 8 of our vulnerabilities were rated as “1337 vulns” and 2 rated as “Rabble Rouser” vulns, more than anyone else in the competition :)
It's official. Team @Secarma has won the #IoT#0Day comp @defcon with the most leet vulns discovered in the last 4 years. Well done team! pic.twitter.com/htBEFtbVCI
— Mr.H (@PRWHarris) September 8, 2017
Since the competition has ended, we have found that the team has had a fair bit of publicity, and we have had the chance to speak to a few people about the state of IOT security, including:
The Mayor of Manchester:


The Manchester Evening News:
http://www.manchestereveningnews.co.uk/business/team-ethical-hackers-manchester-beat-13618798
Business Cloud Magazine:

BBC Click:
Meet one of the teams competing in the #DEFCON25 IoT CTF competition - where they spend three days straight attempting to hack all they can! pic.twitter.com/iRyqEeao63
— BBC Click (@BBCClick) July 28, 2017
and The Independent:
And to top it all off, we received this shiny award this week from SOHOpelesslyBroken
Our shiny trophy arrived today, all the way from @defcon, Vegas. (Did we tell you how we went out there and won?) https://t.co/GYWJjpkDZxpic.twitter.com/QKKdt8nbJj
— Secarma (@Secarma) October 31, 2017
We are working with vendors at the moment to try and ensure that as many of the bugs found are fixed as soon as possible. Once we are confident that the issues have been remediated, we are looking to disclosure the technical details over on Secarma Labs…
